Introduction to DevSecOps
What is DevSecOps?
Definition and Evolution from DevOps: DevSecOps is an extension of DevOps principles, where security (Sec) is integrated into the development (Dev) and operations (Ops) process from the outset. This approach aims to bridge traditional gaps between IT and security while ensuring fast, safe delivery of code. The evolution from DevOps to DevSecOps reflects a shift in mindset from security being a final checkpoint to a continuous consideration throughout the software development lifecycle (SDLC).
Importance in the Modern Software Development Lifecycle (SDLC): In today's fast-paced digital environment, where new software releases are expected rapidly, the traditional approach of applying security measures at the end of the development process is no longer viable. DevSecOps ensures that security is an integral part of the development process from the beginning, enabling teams to detect and address vulnerabilities early, reduce risks, and comply with regulatory requirements efficiently.
Why DevSecOps?
Increasing Security Challenges in Software Development: The complexity of modern software systems and the increasing sophistication of cyber threats have made security a critical concern. Data breaches can lead to significant financial losses, damage to reputation, and legal consequences. DevSecOps addresses these challenges by embedding security practices into the DevOps workflow, reducing the attack surface and making security an ongoing part of the development process.
The Cost of Security Breaches vs. Early Security Integration: The cost of addressing security issues after a product's release can be astronomically higher than integrating security measures during the development phase. Not only are there potential financial penalties associated with breaches, but the cost of remediation, including patches and updates, can disrupt operations and damage customer trust. DevSecOps mitigates these risks by ensuring that security considerations are part of the development process, leading to more secure products and a reduction in post-release security costs.
DevSecOps vs. DevOps
The Integration of Security into DevOps Practices: The key difference between DevOps and DevSecOps lies in the explicit focus on security. While DevOps emphasizes speed, efficiency, and collaboration between development and operations, DevSecOps extends these principles by making security a shared responsibility of all stakeholders involved in the development process. This integration ensures that security considerations are not sidelined or treated as an afterthought but are an integral part of the development, delivery, and maintenance of software solutions.
Foundations of DevSecOps
Security as Code
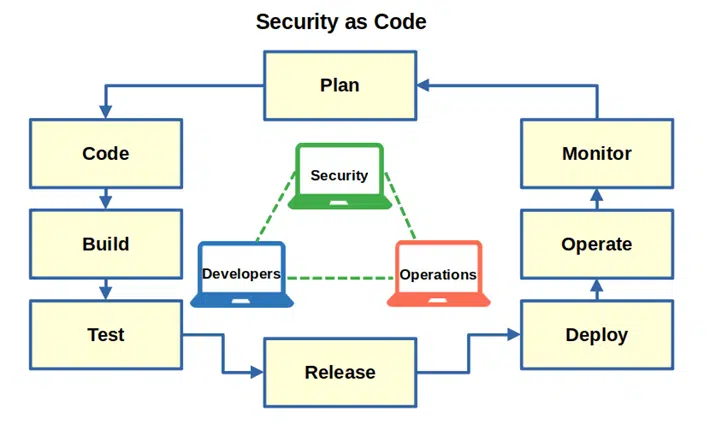
Security as Code (SaC) is about integrating security measures and policies directly into the development and deployment processes. It involves defining security practices and configurations as code, making it easier to distribute, version control, and manage security alongside the application code. This approach ensures consistency across environments and facilitates automated security checks.
Example: Implementing Infratructure as Code with Security Policies
Consider a scenario where you're deploying a set of cloud resources using Terraform, an Infrastructure as Code (IaC) tool. You want to ensure that all resources comply with your organization's security policies, such as restricting SSH access and enforcing encryption.
resource "aws_vpc" "main" {
cidr_block = "10.0.0.0/16"
}
resource "aws_security_group" "allow_ssh" {
vpc_id = aws_vpc.main.id
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "Allow SSH"
}
}
resource "aws_s3_bucket" "data" {
bucket = "my-secure-bucket"
acl = "private"
server_side_encryption_configuration {
rule {
apply_server_side_encryption_by_default {
sse_algorithm = "AES256"
}
}
}
tags = {
Environment = "Production"
}
}
In this Terraform script:
An AWS VPC is created with a specific CIDR block.
A security group allowing SSH access from anywhere is defined, which should be restricted based on the principle of least privilege.
An S3 bucket with server-side encryption enabled showcases how to enforce data encryption.
By codifying these security settings, teams ensure that every deployment adheres to predefined security standards, significantly reducing the risk of human error or oversight.
Automation in DevSecOps
Automation is key in DevSecOps, enabling the seamless integration of security checks into the software development lifecycle. Automated security testing tools can identify vulnerabilities early in the development process, making remediation more manageable and less costly.
Example: Automating Security Scans in CI/CD Pipelines
Consider integrating automated security scanning into a Jenkins CI/CD pipeline. Jenkins, a widely used automation server, supports various plugins to automate building, testing, and deploying applications. Here's how you can integrate a Static Application Security Testing (SAST) tool into a Jenkins pipeline:
pipeline {
agent any
stages {
stage('Checkout') {
steps {
checkout scm
}
}
stage('Build') {
steps {
echo 'Building...'
// Your build commands go here
}
}
stage('Security Scan') {
steps {
echo 'Running security scan...'
sh 'find . -name "*.java" | xargs sonar-scanner'
}
}
stage('Deploy') {
steps {
echo 'Deploying...'
// Your deployment commands go here
}
}
}
post {
always {
echo 'Cleaning up...'
// Cleanup actions go here
}
success {
echo 'Build and deployment successful!'
}
failure {
echo 'An error occurred. Check the logs for details.'
}
}
}
In this Jenkins pipeline configuration:
The
Checkoutstage retrieves the latest code from the source control management (SCM) system.The
Buildstage compiles the application code, preparing it for deployment.The
Security Scanstage executes a security scanning tool (e.g., SonarQube) against the codebase, looking for potential vulnerabilities in the.javafiles. This stage illustrates how security checks are seamlessly integrated into the pipeline, ensuring that every build is automatically scanned for security issues.The
Deploystage pushes the build to a production or staging environment, assuming the security scan passes.
This automation ensures that security scanning is an integral part of the development process, not a separate or manual step, thereby enhancing the security posture without sacrificing speed or efficiency.
CI/CD Integration
Continuous Integration and Continuous Deployment (CI/CD) are practices that allow for the frequent integration of code changes into a shared repository and automatic deployment to production environments. Integrating security into CI/
CD pipelines ensures that security checks are performed automatically and consistently.
Detailed Insight: Security Gates in CI/CD Pipelines
Incorporating "security gates" into CI/CD pipelines involves setting specific criteria that code changes must meet before moving to the next stage of the pipeline. For instance, a security gate may require that all high-severity vulnerabilities identified by a SAST tool be addressed before code is allowed to merge into the main branch or be deployed to production.
Implementing security gates involves configuring your CI/CD tooling to:
Run automated security tests at predetermined points in the pipeline.
Evaluate the results of these tests against predefined criteria (e.g., no critical vulnerabilities).
Halt the progression of the pipeline if the criteria are not met, requiring intervention to resolve the identified security issues.
This approach ensures that only secure, vetted code is deployed, significantly reducing the risk of introducing security vulnerabilities into production environments.
Collaboration & Communication
DevSecOps fosters a culture where development, operations, and security teams work closely together, sharing responsibility for security and ensuring that it is not siloed. This collaboration is facilitated by open communication channels and shared tools.
Case Studies: Companies That Successfully Implemented a DevSecOps Culture:
Etsy: As one of the early adopters of DevOps, Etsy successfully integrated security into their DevOps practices by developing and sharing internal tools for continuous integration and deployment. Their approach to automated security testing and monitoring has been influential in the DevSecOps community.
Netflix: Known for its cutting-edge use of technology, Netflix has also been a pioneer in adopting DevSecOps. They developed several in-house tools, such as the fully automated, self-service Simian Army, to ensure the security and reliability of their massive cloud-based architecture.
Technical Deep Dive into DevSecOps
The technical implementation of DevSecOps involves integrating a suite of tools and practices into the development and deployment pipeline to ensure security is continuously addressed. This section delves into the specifics of integrating security tools, adopting secure coding practices, managing application dependencies, and ensuring container and cloud security.
Integrating Security Tools into the CI/CD Pipeline

The integration of security tools into the CI/CD pipeline is crucial for automating security checks and tests. This automation helps identify vulnerabilities early in the development process, facilitating rapid remediation.
Selection of Tools:
Static Application Security Testing (SAST): SAST tools analyze source code at rest to detect vulnerabilities without executing the code. For instance, integrating a tool like SonarQube into a Jenkins pipeline involves steps where SonarQube scans are triggered automatically during code builds. The results can pinpoint exact lines of code with potential security issues, such as SQL injection risks or cross-site scripting (XSS) vulnerabilities.
Example: This Jenkins pipeline configuration demonstrates the integration of SonarQube for automated security scanning within the CI/CD process. It's crucial that the SonarQube server is correctly configured and that the
SonarScannertool is available in the Jenkins environment.pipeline { agent any stages { stage('Checkout') { steps { checkout scm } } stage('Build') { steps { sh './gradlew clean build' } } stage('SonarQube Analysis') { steps { script { scannerHome = tool 'SonarScanner'; withSonarQubeEnv('My SonarQube Server') { sh "${scannerHome}/bin/sonar-scanner" } } } } } }Dynamic Application Security Testing (DAST): DAST tools interact with applications in their running state to identify vulnerabilities. Integrating DAST tools like OWASP ZAP into CI/CD pipelines enables automated security testing on deployed applications. This can be particularly useful for identifying runtime issues that SAST might miss, such as authentication problems or session management issues.
Integration with CI/CD:
Using OWASP ZAP with Jenkins can involve setting up a stage in the pipeline where ZAP conducts active scans against a deployed instance of the application. The results can then be reviewed to identify and mitigate any security vulnerabilities detected during the dynamic analysis.
Infrastructure as Code (IaC) Scanning: Tools like Terraform and Checkov scan IaC for misconfigurations and compliance with security best practices.
Secure Coding Practices

Secure coding practices are preventive measures taken to eliminate vulnerabilities at the code level, ensuring the software is resilient to attacks.
Security Guidelines for Developers:
- Adopting coding standards that emphasize security, such as OWASP’s Top Ten, helps developers avoid common security pitfalls.
Common Security Pitfalls and How to Avoid Them:
SQL Injection: One of the most critical security flaws in web applications. Using parameterized queries is a fundamental practice to prevent SQL injections.
Example: This example uses
PreparedStatementin Java to safely include user input in a SQL query, effectively mitigating SQL injection risks.String query = "SELECT account_balance FROM user_data WHERE user_name = ?"; try (PreparedStatement pstmt = connection.prepareStatement(query)) { pstmt.setString(1, username); ResultSet rs = pstmt.executeQuery(); while (rs.next()) { // Process the result } }Cross-Site Scripting (XSS): Employ content security policies and sanitize input to prevent malicious scripts from executing.
Example: This JavaScript function demonstrates a basic approach to sanitizing input by removing potential script tags and other HTML elements that could be used to execute XSS attacks.
function sanitizeString(str) { return str.replace(/<script[^>]*>([\S\s]*?)<\/script>/gmi, '') .replace(/<\/?\w(?:[^"'>]|"[^"]*"|'[^']*')*>/gmi, ''); }
Security in Application Dependencies
Managing the security of application dependencies involves monitoring and updating libraries and frameworks to patch vulnerabilities.
Managing Third-Party Vulnerabilities:
- Tools like Snyk and Dependabot automatically scan project dependencies for known vulnerabilities and can be integrated into CI/CD pipelines to ensure up-to-date and secure dependencies.
Tools for Dependency Scanning and Management:
Example: Using Dependabot with GitHub Actions to automate dependency updates.
GitHub's Dependabot scans your dependencies for known vulnerabilities and creates pull requests to update them to more secure versions.
version: 2 updates: - package-ecosystem: "npm" directory: "/" schedule: interval: "weekly" open-pull-requests-limit: 10This
.github/dependabot.ymlconfiguration file instructs Dependabot to check npm dependencies on a weekly basis and limits the number of open pull requests to 10, preventing overwhelming developers.
Container Security

Containers, while improving deployment efficiency and scalability, introduce new security challenges that need to be addressed.
Best Practices for Docker, Kubernetes:
- Ensure images are sourced from trusted registries, use minimal base images, and regularly scan images for vulnerabilities.
Tools for Container Scanning and Management:
Tools like Trivy or Clair scan container images for vulnerabilities. Integrating these tools into CI/CD pipelines ensures that images are scanned before deployment.
Trivy Integration Example:
image --severity HIGH,CRITICAL myapplication:latestThis command line example uses Trivy to scan the
myapplication:latestimage for high and critical severity vulnerabilities, which can be part of a CI pipeline step to ensure only secure containers are deployed.
Cloud Security

Securing cloud environments is paramount as more organizations adopt cloud services for their flexibility and scalability.
Security Considerations in Cloud Environments:
- Apply the principle of least privilege, encrypt data at rest and in transit, and use identity and access management (IAM) to control access.
Cloud-Specific Security Tools and Practices:
- Cloud service providers offer native tools (e.g., AWS Security Hub, Azure Security Center) that provide security assessments and recommendations.
Advanced Topics and Future Trends in DevSecOps
As DevSecOps matures, several advanced topics and future trends are shaping its evolution, offering new opportunities and challenges. This section explores the integration of machine learning and AI, the implications of microservices and serverless computing, and the future directions of DevSecOps.
Machine Learning and AI in DevSecOps
Automating Threat Detection: Machine learning algorithms can analyze vast amounts of data to detect patterns and anomalies that may indicate security threats. By integrating AI-driven tools into DevSecOps workflows, organizations can automate the detection of complex security threats that traditional tools might miss.
Real-Life Example: Netflix uses machine learning in its risk assessment and user behavior analysis to detect anomalous patterns that could indicate security threats. Their machine learning models are trained on a dataset comprising both normal user activities and various attack vectors, enabling the system to detect and respond to threats in real time.
Code Snippet for Anomaly Detection: This simplistic example demonstrates using the Isolation Forest algorithm, a type of machine learning model that isolates anomalies instead of profiling normal data points, which is particularly useful in detecting unusual patterns in network traffic that could signify a security threat.
from sklearn.ensemble import IsolationForest from sklearn.preprocessing import StandardScaler # Sample dataset: network traffic features X = [[-1.1], [0.3], [0.5], [100], [0.4], [0.8], [1.2], [90]] # Normalize the data X = StandardScaler().fit_transform(X) # Train the model clf = IsolationForest(random_state=42) clf.fit(X) # Predict anomalies predictions = clf.predict(X) # Output: 1 for normal, -1 for anomaly print(predictions)
Predictive Analytics for Security Vulnerabilities: AI can predict potential vulnerabilities and threats by analyzing code changes, historical breach data, and emerging trends in cybersecurity. This predictive capability allows organizations to proactively address security risks before they are exploited.
Example: Implementing a simple predictive model using Python to analyze code commit messages for potential security implications.
from sklearn.feature_extraction.text import TfidfVectorizer from sklearn.naive_bayes import MultinomialNB from sklearn.pipeline import make_pipeline # Sample data (commit messages and associated risk levels) commit_messages = ["Fix security issue with user authentication", "Update README", "Patch XSS vulnerability in comment section", "Add new user profile fields"] risk_levels = [1, 0, 1, 0] # 1 for high-risk, 0 for low-risk # Create a model pipeline model = make_pipeline(TfidfVectorizer(), MultinomialNB()) # Train the model model.fit(commit_messages, risk_levels) # Predict the risk level of a new commit message new_messages = ["Implement new encryption for database"] predicted_risk = model.predict(new_messages) print("Predicted Risk Level:", "High" if predicted_risk[0] == 1 else "Low")This simplistic example uses a Naive Bayes classifier to predict the risk level of code commits based on their messages, demonstrating how AI can be leveraged to identify potential security concerns automatically.
DevSecOps in the Era of Microservices and Serverless Computing
Specific Challenges and Solutions: The shift towards microservices and serverless architectures introduces new security challenges, such as increased attack surfaces and the complexity of managing distributed systems.
- Real-Life Example: An online media streaming service transitioned to a microservices architecture to improve scalability and development speed. To address the associated security challenges, they implemented a service mesh that provided consistent security policies, encryption, and access control across services.
Case Examples of Security in Microservices Architecture: Ensuring security in a microservices architecture requires a comprehensive strategy that includes securing inter-service communications, managing secrets, and implementing robust access controls.
Code Example: Using HashiCorp Vault for managing secrets in a microservices environment.
# Initialize Vault vault operator init # Store a secret vault kv put secret/my_service/api_key value="s3cr3t" # Retrieve a secret vault kv get secret/my_service/api_keyThis example shows basic commands to store and retrieve secrets using Vault, demonstrating how DevSecOps practices can manage sensitive information securely in a distributed architecture.
Tools for DevSecOps
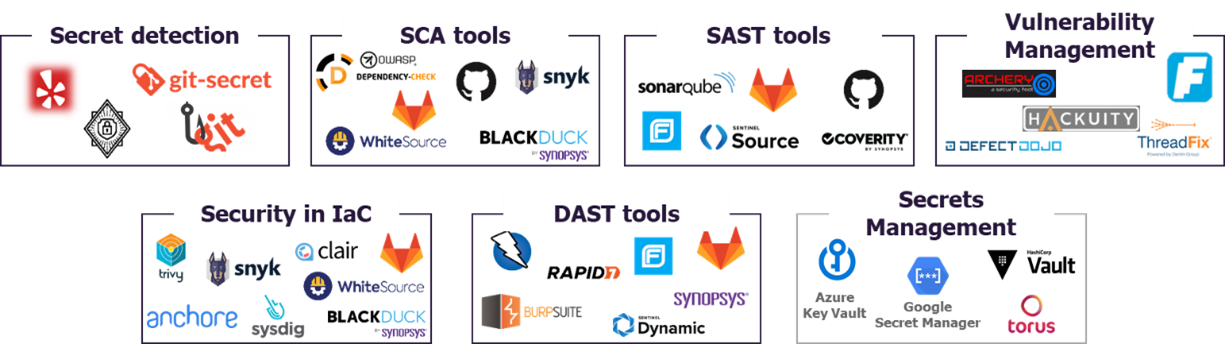
DevSecOps tools can be categorized based on their functionality and the stage of the CI/CD pipeline they support. Here's an overview:
Static Application Security Testing (SAST):
SonarQube: Integrates with CI/CD pipelines to analyze source code for vulnerabilities.
Checkmarx: Offers comprehensive code analysis for identifying security issues.
Dynamic Application Security Testing (DAST):
OWASP ZAP: An open-source tool for automatically finding security vulnerabilities in web applications.
Burp Suite: A popular tool for web application security testing.
Software Composition Analysis (SCA):
Snyk: Identifies known vulnerabilities in dependencies.
WhiteSource: Automates the entire process of open-source component selection, approval, and management.
Infrastructure as Code (IaC) Scanning:
Terraform: Provides IaC services with security-focused modules.
Checkov: A static code analysis tool for infrastructure as code (IaC).
Container Security:
Clair: An open-source project for the static analysis of vulnerabilities in application containers.
Aqua Security: Provides full lifecycle security for containerized applications.
Secrets Management:
HashiCorp Vault: Secures, stores, and tightly controls access to tokens, passwords, certificates, API keys, and other secrets.
AWS Secrets Manager: Helps manage, retrieve, and store secrets securely.
Security Orchestration, Automation, and Response (SOAR):
Demisto (now part of Palo Alto Networks): Combines security orchestration, incident management, and interactive investigation.
IBM Resilient: Provides orchestration and automation to streamline incident response.
Conclusion
In conclusion, DevSecOps marks a transformative shift towards embedding security within the very fabric of the software development lifecycle. This exploration highlights the vital importance of integrating security from the outset, thus enabling organizations to not only preemptively address vulnerabilities but also foster a culture of proactive security mindfulness. By weaving security into every stage of development, from initial design to deployment, organizations can significantly mitigate risks, enhance efficiency, and build stronger trust with their stakeholders.
The journey to adopting DevSecOps is ongoing, characterized by continuous learning, adaptation, and improvement. As we've seen through practical examples, the adoption of DevSecOps practices equips organizations to face evolving cybersecurity challenges with agility and resilience. Looking ahead, the principles of DevSecOps will continue to guide the future of software development, ensuring that security remains at the forefront of technological innovation and organizational strategy. Embracing DevSecOps is not just a necessity but a strategic advantage in the digital age, paving the way for safer, more secure software solutions.

Thank you for reading this Blog. Hope you learned something new today! If you found this blog helpful, please like, share, and follow me for more blog posts like this in the future.
If you have some suggestions I am happy to learn with you.
I would love to connect with you on LinkedIn
Meet you in the next blog....till then Stay Safe ➕ Stay Healthy
#HappyLearning #devops #DevSecOps #CyberSecurity #CloudSecurity #SoftwareDevelopment #InfoSec #TechTrends #DigitalTransformation #AIinSecurity #ContainerSecurity #SecureCoding #TechInnovation #CodingBestPractices #SAST #DAST #IaC #ContinuousIntegration #ContinuousDeployment #AutomationInSecurity #ThreatDetection #VulnerabilityManagement #SecurityAutomation #MicroservicesSecurity #ServerlessSecurity #QuantumComputingSecurity #DataProtection #IdentityManagement #AccessControl #TechCommunity #SoftwareEngineers #DevOpsEngineers #SecurityProfessionals #ITSecurity #CloudComputing #EmergingTech #FutureOfTech #TechNews
