Empowering Secure User Impersonation: Leveraging Azure Monitor Logs and Azure AD for Enhanced Auditing and Identity Management
User impersonation and logging are crucial for the seamless operation and security of software applications. Microsoft's Azure brings to the table robust tools for both these tasks. Let's journey through the intricacies of user impersonation in the context of Azure Monitor Logs.
User Impersonation Deep Dive
What Exactly is User Impersonation?
User impersonation is the capability where a user (often an administrator) assumes the identity and rights of another user. While it seems straightforward, the implications and applications are wide-ranging.
Key Uses:
Administrative Tasks: For applying specific changes to a user account without requiring their credentials.
Issue Troubleshooting: Replicating issues that are user-specific.
Granular App Testing: Ensuring the app functions appropriately across different user roles.
The Technicals of User Impersonation
To achieve impersonation in applications, systems often adjust the user context for the duration of a session.
Sample C# Code:
public class UserImpersonation
{
private IIdentity originalIdentity;
public bool ImpersonateUser(string username)
{
originalIdentity = HttpContext.Current.User.Identity;
// Logic to switch to the new user's identity
var impersonatedIdentity = new GenericIdentity(username);
HttpContext.Current.User = new GenericPrincipal(impersonatedIdentity, null);
return true;
}
public void RevertImpersonation()
{
HttpContext.Current.User = new GenericPrincipal(originalIdentity, null);
}
}
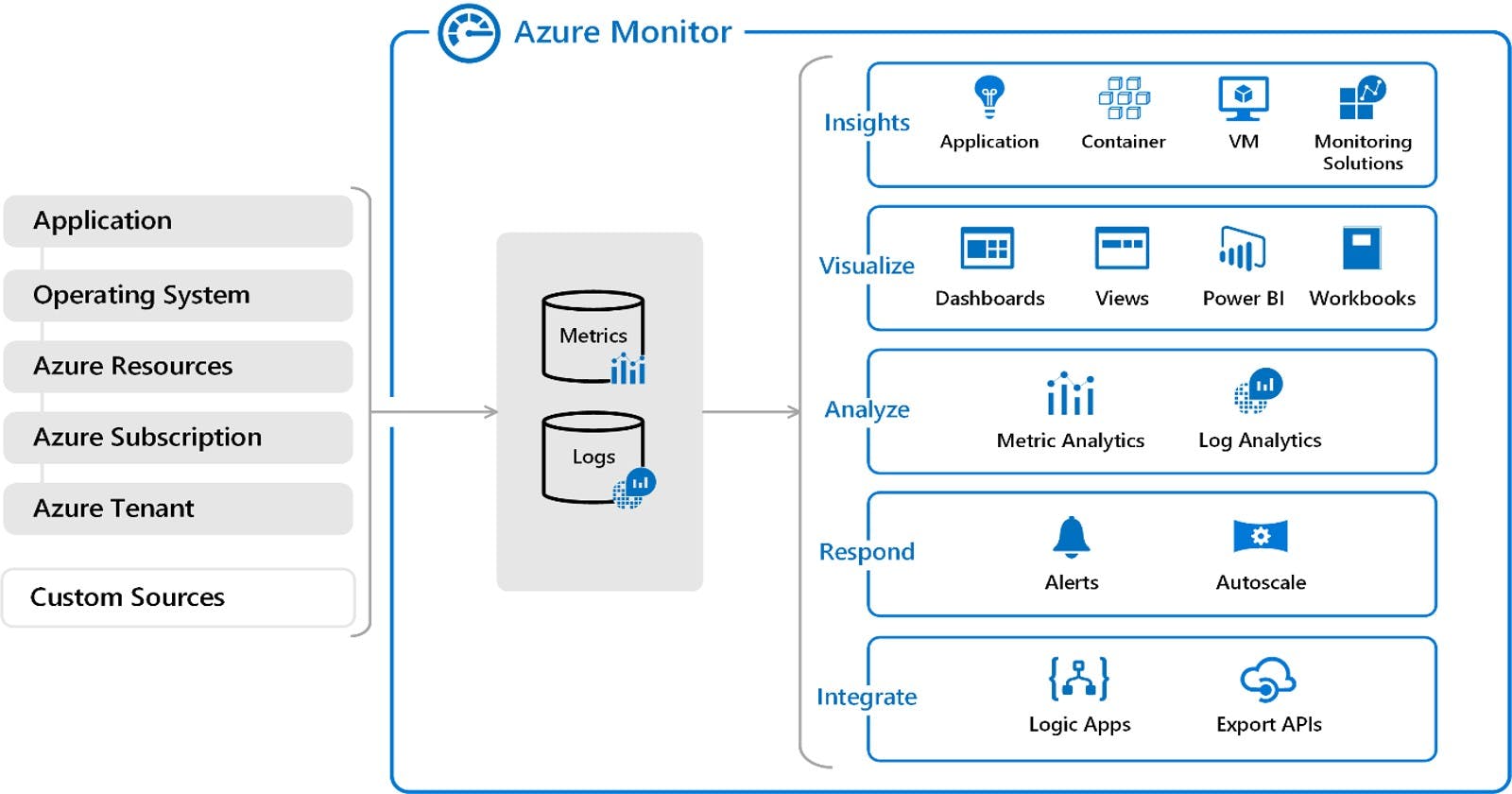
Azure Monitor Logs: A Primer

Azure Monitor Logs, an integral part of Azure Monitor, provides advanced analytics and intelligent alerting on your data. It collects large amounts of fast-streaming data, correlates it, and transforms this data into actionable insights.
The Basics
Data Collection: From applications, infrastructure, and network on Azure and other environments.
Log Analytics: Perform ad-hoc querying and analysis on stored data.
Intelligent Insights: Using advanced analytics and machine learning.
Writing Impersonation Logs to Azure Monitor
Every impersonation event should be logged for auditing purposes. Azure Monitor Logs facilitates this.
Sample C# Logging Logic:
public class ImpersonationLogger
{
public async Task LogImpersonationAsync(int adminId, int impersonatedUserId)
{
var logData = new
{
AdminId = adminId,
ImpersonatedUserId = impersonatedUserId,
Timestamp = DateTime.UtcNow
};
// Assuming a hypothetical AzureMonitor API
await AzureMonitorLogsApi.WriteAsync(logData, "ImpersonationEvents");
}
}
Why User Impersonation with Azure Monitor Logs?
Enhanced Auditing:
User impersonation inherently possesses the potential risk of misuse. Azure Monitor Logs provides a comprehensive logging system that helps track every impersonation event in detail. This ensures transparency and accountability.
Benefits:
Traceability: Every impersonation action is traceable back to its originator.
Forensics: In case of any security event, detailed logs assist forensic analysis, helping in understanding the breach and preventing future ones.
Compliance: Many industries have stringent data handling and processing standards. Detailed logging ensures adherence to such standards.
Real-time Alerts:
Azure Monitor Logs isn't just about passive logging; it’s about real-time insights. If there are unusual patterns in impersonation – like a high frequency of impersonation events or events at odd hours – alerts can be triggered.
Benefits:
Prompt Response: Instantaneous alerts ensure immediate action on suspicious activities.
Security Posture: Continuous monitoring elevates an organization's overall security posture.
Azure AD (AAD) & Its Interplay with Impersonation

Azure Active Directory (AAD) is Microsoft's cloud-based identity and access management service. It integrates with Azure Monitor Logs for enhanced security during impersonation.
Impersonation Using Azure AD
AAD supports OAuth 2.0's On-Behalf-Of flow, granting one service an access token to another service on behalf of a user.
Sample Token Acquisition Code:
var userAssertion = new UserAssertion(userToken, "urn:ietf:params:oauth:grant-type:jwt-bearer", userEmail);
var result = await authenticationContext.AcquireTokenAsync(targetApiId, clientCredential, userAssertion);
Why User Impersonation with Azure AD (AAD)?
Azure AD is not just an identity service; it's a comprehensive identity solution. When user impersonation is backed by Azure AD, it ensures that the entire process is governed by a robust identity system.
Seamless & Secure Transition:
Azure AD’s OAuth 2.0 On-Behalf-Of flow allows for a seamless transition from one identity to another, ensuring that the impersonation is both efficient and secure.
Benefits:
Multi-Factor Authentication (MFA): Before an impersonation session begins, AAD can mandate MFA for the admin, adding an extra security layer.
Role-Based Access Control (RBAC): Only designated roles can perform impersonation, minimizing the risk of unauthorized impersonation.
Integrated Management:
With Azure AD, the management of impersonation permissions becomes an integrated part of the organization's identity management process.
Benefits:
Consolidated Management: No need for separate tools or platforms; everything related to user identities and permissions, including impersonation, can be managed from a single dashboard.
Conditional Access Policies: Impersonation can be bound by conditions, like location or device status, further refining its security.
Enhanced Security & Auditing with Azure Monitor Logs

With Azure Monitor Logs, you can establish alert rules on your logging data, giving an edge to security.
Setting Up Alert Logic
For instance, to get alerts on impersonation outside working hours, you'd use:
ImpersonationEvents
| where Timestamp > ago(1h)
| where HourOfDay !between(9..17)
| project AdminId, ImpersonatedUserId, Timestamp
Upon executing this Kusto Query Language (KQL) script, you'll receive alerts on any anomalies.
Best Practices & Precautions
Permission Restrictions: Only grant impersonation rights to trusted roles.
Impersonation Notification: Notify users when their accounts are being impersonated.
Time-bound Sessions: Limit the duration of impersonation to prevent prolonged unauthorized access.
Comprehensive Auditing: Use Azure Monitor Logs to maintain a thorough record of all impersonation events.
Conclusion
User impersonation, while instrumental, mandates judicious and secured deployment. Azure provides a comprehensive suite, from Azure AD for authentication to Azure Monitor Logs for auditing, ensuring a balance between functionality and security. This guide, replete with examples, serves as a solid foundation for those venturing into user impersonation and monitoring with Azure.

Thank you for reading this Blog. Hope you learned something new today! If you found this blog helpful, please like, share, and follow me for more blog posts like this in the future.
If you have some suggestions I am happy to learn with you.
I would love to connect with you on LinkedIn
Meet you in the next blog....till then Stay Safe ➕ Stay Healthy
#HappyLearning #devops #AzureMonitorLogs #AzureAD #UserImpersonation #Cybersecurity #IdentityManagement #Auditing #AzureSecurity #BestPractices #CloudComputing #MicrosoftAzure #OAuth2 #RealTimeAlerts #RBAC #MFA #ConditionalAccess #Compliance #AzureIntegration #AzureLogging #Forensics #ITSecurity